/
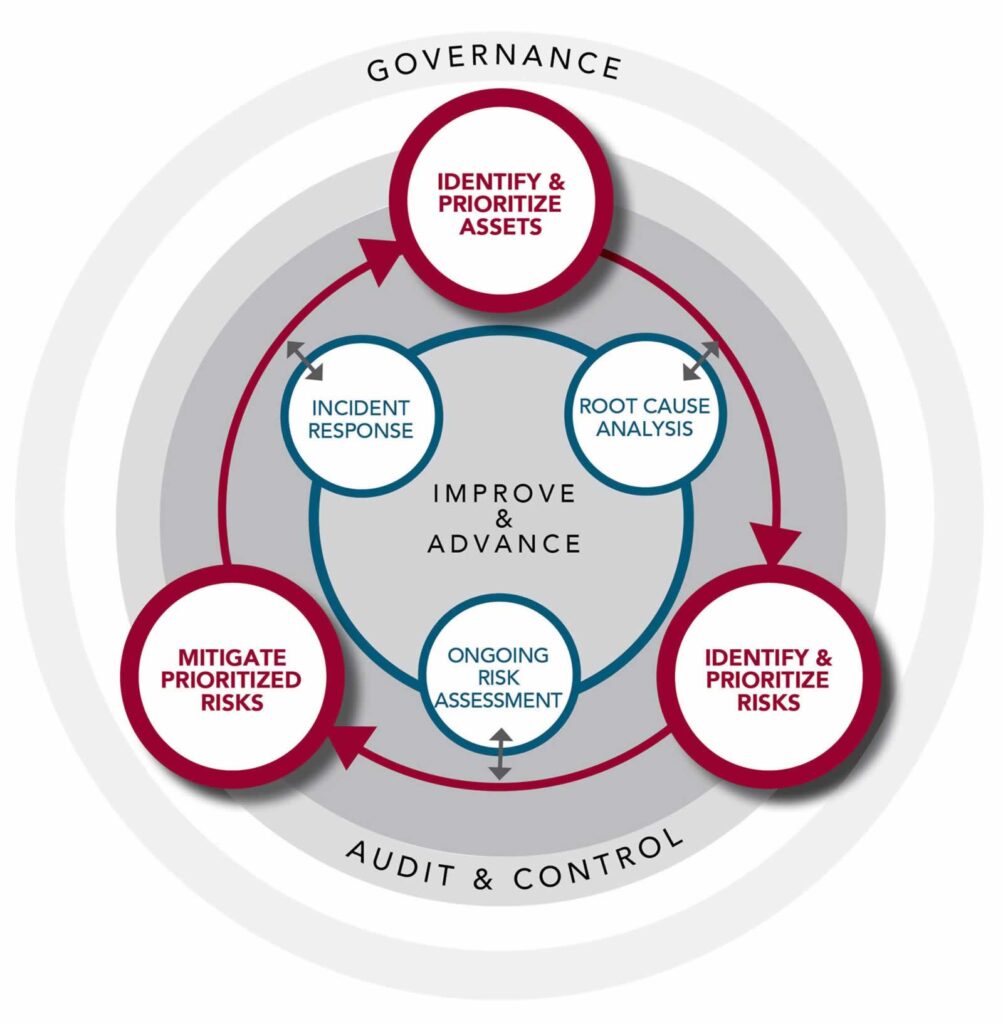
Governance
Governance plays a dominant role throughout the ESRM process. The process identifies asset owners and stakeholders, engages them in a thoughtful dialogue designed to identify a proper risk appetite for the enterprise, and aligns mitigation and risk acceptance efforts to fit the enterprise risk tolerance level.
Audit & Control
Transparency throughout the ESRM process is critical for success. Applying independent audit and controls to measure the ESRM approach and effectiveness during the entire process provides for proper accountability and unprejudiced reporting.
Improve & Advance
The risk paradigm as it applies to managing security risks is an ongoing and thoughtful approach to security. It demands a perpetual cycle of thought and application to the security practice to continuously improve and advance the security risk posture of the enterprise.
Identify & Prioritize Assets
The process of identifying and prioritizing the enterprises’ assets. People, process, information, facilities, its reputation, regulatory obligations, really anything of value. This is done in conjunction with the prioritization of those assets using various techniques such as a business impact analysis or simply working with the business to understand their value and potential disruptive effect on the business mission and goals.
Identify and Prioritize Risks
Association of risks to an asset is critical to understanding the relationship of risk to the assets value. It will identify probability and potential impact on that asset furthering an understanding on how to prioritize the associated risks.
Mitigate Prioritized Risks & Acceptance
Mitigation planning, execution, and risk acceptance are mostly what are perceived as our ‘tasks’. The ‘tasks’ are identified as physical security, information security, cybersecurity, business continuity, etc. These responsibilities are always associated with the surrounding risk principles that give the tasks purpose and align those tasks as part of a role.
Root Cause Analysis
Any security event that is relevant to the assets of the organization and the risks associated with those assets, no matter if it happened inside the organization or not, should always follow a process identifying any residual risks or a change in risks to those assets.
Ongoing Risk Assessment
On an ongoing basis, risks will continuously evolve and expose themselves. Some of those risks have never been identified or perceived, and other times the value of assets change, which changes the association of already identified and prioritized risks. Continuously monitoring the changing risk landscape and applying the risk knowledge to the identified risks and prioritized assets is an ongoing process.
Incident Response
Investigations, data forensics, and crisis management are forms of incident response and are often seen as particular tasks. Incident response is a planned or impromptu response to the interaction of an asset and risk that has become realized.